Event: OWASP x Horizon
Category: Forensic
Challenge: corrupted
Challenge Description:
Alice sent the image to Bob but the image is corrupted, recover the original image and find the flag from the image.
Author - DIVAS
Solution:
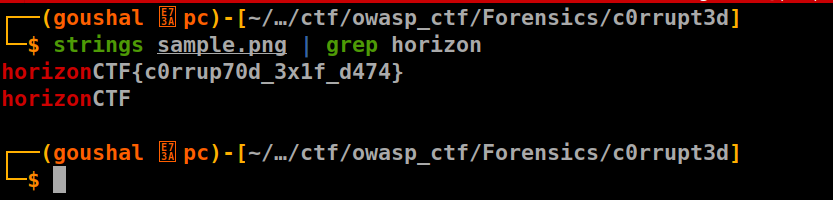
This challenge is very easy. Before getting into any steg tool, I used strings to extract any string that had horizon in it and grepped it so that I could get the flag because the format of the flag is horizonCTF{}.
Category: Forensic
Challenge: Finding the Hidden Flag
Challenge Description:
Analyze the provided pcap file to find the hidden encflag. The flag is encrypted with an XOR cipher and is located in a packet sent to port 12345. Decrypt the flag using the provided key and submit it in the format flag{...}.
Author- Abishek
Files: challenge.pcapng , decrypt.py
Solution:
After opening the challenge.pcapng file using Wireshark there were over 2000+ packets but still I went through a few packets and got a fake flag:
flag{m6yb3_i_am_the_Fl4g}
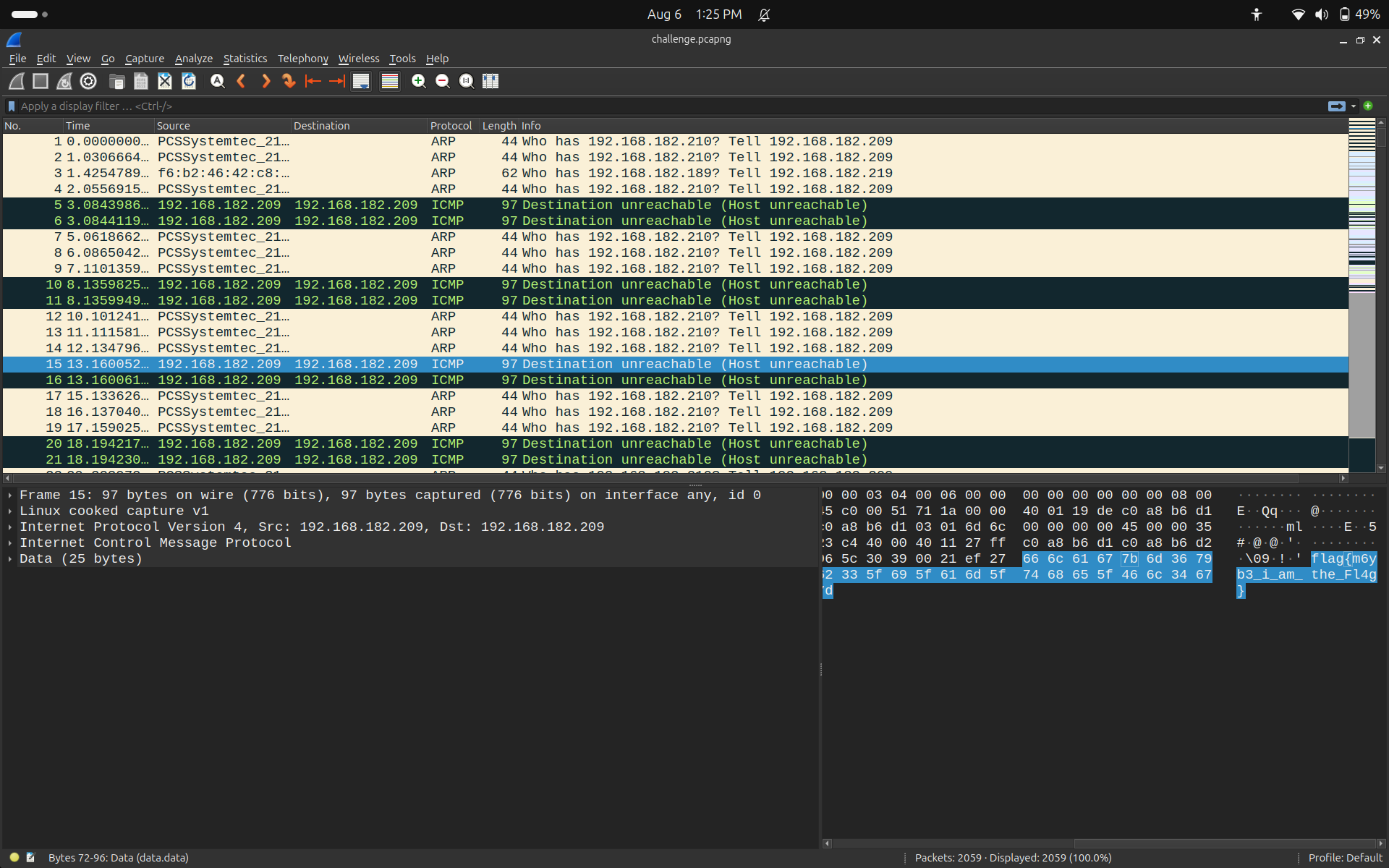
In the description, it is given that they have encrypted it in XOR. In the terminal, I used strings challenge.pcapng | grep flag. After using the command, I found something suspicious encflag{. To get the raw data, I built a Python tool called Packet_reader. After extracting all the raw data, I found the encflag:
encflag{\n\x1a\x06/\x07\x0e\x1e\x0e:\t\x10\x14\x03/\x05\x0e\x02\x0e\x0b\n\x1a\x16}
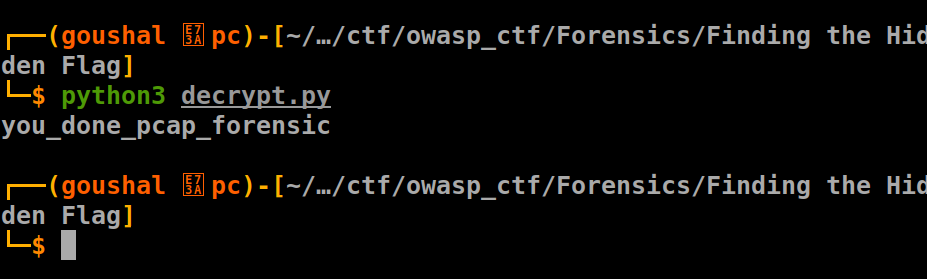
and found the key in the same way key = suspcapkeyx. Use the decrypt.py to get the flag:
horizonCTF{you_done_pcap_forensic}
Category: Forensic
Challenge: stegloop
Challenge Description:
Alice knows that the flag is hidden inside the image and there is a bunch of passwords in a list. Would you help Alice find the flag?
Files: artic.jpg, wordlist.txt

Solution:
In the description, I saw a bunch of passwords and a wordlist.txt in the given files. As soon as I saw that, I knew that this was a stegcrack challenge. I used stegcracker and with the help of the tool, I cracked the password using the command:
stegcracker artic.jpg wordlist.txt -V -o flag.txt
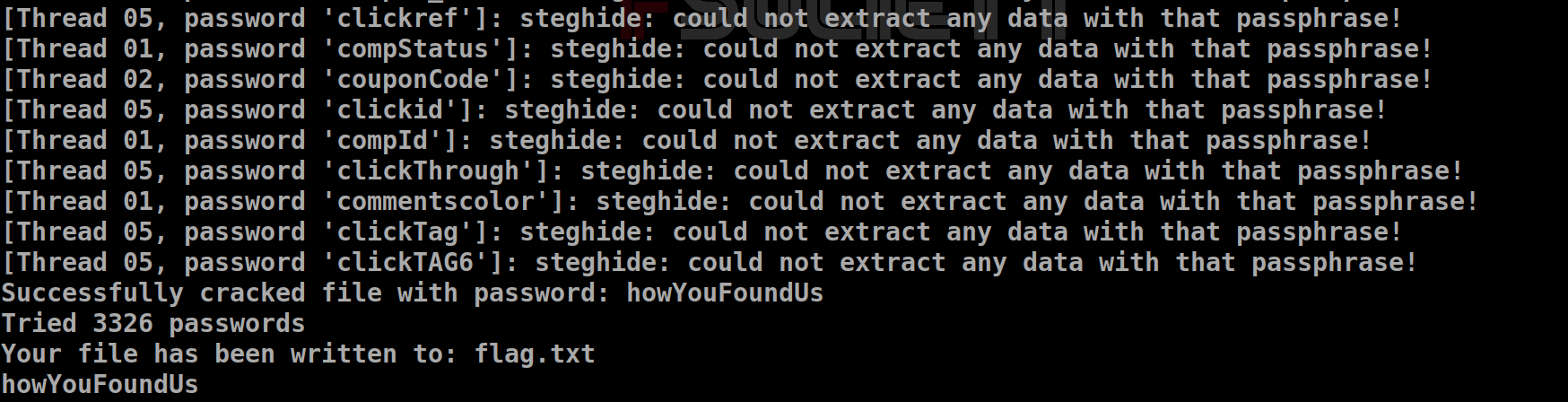
After cracking the password, I found the flag:
horizonCTF{5t3g_4r3_50_fun}
Category: Reversing
Challenge: javafuck
Challenge Description:
java java javascript
Author jones
Files: 1.html
Solution:
const rotateArray = function(array, count) {
while (--count) {
array.push(array.shift());
}
};
const _0x59d7 = [
'0x13f', 'value', 'getElementById',
'Correct password! Flag:', 'Incorrect password',
'pwd', 'map', 'charCodeAt', 'length',
'from', 'filter', 'push', 'shift', 'while', 'return'
];
rotateArray(_0x59d7, 0x15f);
const _0x3c9f = function(index) {
index = index - 0x0; // Normalize the index
return _0x59d7[index];
};
function xtsca() {
const getValueById = _0x3c9f;
const correctPassword = [
104, 111, 114, 105, // 'hori'
122, 111, 110, // 'zon'
123, 100, 101, // '{de'
51, 109, 95, // '3m_'
99, 48, 48, 108, // 'c00l'
125 // '}'
];
const enteredPassword = document.getElementById('pwd').value;
const enteredPasswordCodes = Array.from(enteredPassword).map(ch => ch.charCodeAt(0));
if (enteredPasswordCodes.length !== correctPassword.length) {
alert('Incorrect password');
return;
}
for (let i = 0; i < enteredPasswordCodes.length; i++) {
if (enteredPasswordCodes[i] !== correctPassword[i]) {
alert('Incorrect password');
return;
}
}
alert('Correct password! Flag:');
}
After opening the 1.html file, I saw that the one function and had a keyword
flag and was entirely obfuscated. After analyzing and deobfuscating
the code, I found that the password was a string of characters that corresponded to ASCII values
deobfuscated code:
const rotateArray = function(array, count) {
while (--count) {
array.push(array.shift());
}
};
const _0x59d7 = [
'0x13f', 'value', 'getElementById',
'Correct password! Flag:', 'Incorrect password',
'pwd', 'map', 'charCodeAt', 'length',
'from', 'filter', 'push', 'shift', 'while', 'return'
];
rotateArray(_0x59d7, 0x15f);
const _0x3c9f = function(index) {
index = index - 0x0; // Normalize the index
return _0x59d7[index];
};
function xtsca() {
const getValueById = _0x3c9f;
const correctPassword = [
104, 111, 114, 105, // 'hori'
122, 111, 110, // 'zon'
123, 100, 101, // '{de'
51, 109, 95, // '3m_'
99, 48, 48, 108, // 'c00l'
125 // '}'
];
const enteredPassword = document.getElementById('pwd').value;
const enteredPasswordCodes = Array.from(enteredPassword).map(ch => ch.charCodeAt(0));
if (enteredPasswordCodes.length !== correctPassword.length) {
alert('Incorrect password');
return;
}
for (let i = 0; i < enteredPasswordCodes.length; i++) {
if (enteredPasswordCodes[i] !== correctPassword[i]) {
alert('Incorrect password');
return;
}
}
alert('Correct password! Flag:');
}
the flag is :horizonCTF{de3m_c00l}